Loading Insight...
Insights
Insights

Amidst escalating cyber threats, the financial sector grapples with vulnerabilities. Dive into the transformative realm of Zero Trust, fortifying defenses and reshaping cybersecurity paradigms.
The financial industry faces a rising threat from cyberattacks, ranking high in reported data breaches. This increase is due to its speedy shift towards digital systems, inadvertently catching the attention of cybercriminals looking for weak spots in these new setups.
With heavy reliance on digital tools and more flexible work setups, there is an urgent need for better security measures. The old ways of defending these systems are not enough against the increasingly sophisticated threats targeting the various parts of the system, which include users, devices, and applications.
To tackle these challenges, a new approach called “Zero Trust” has emerged. It is a big change in how we do cybersecurity. Instead of relying on old-fashioned perimeter defences, Zero Trust acknowledges the limitations of these traditional models and focuses on finding and fixing vulnerabilities that often get overlooked.
This article will dive deeper into the overview of what Zero Trust is and how adapting a Zero Trust framework can make your organisation more secure.
Evolution and milestones of Zero Trust
Zero Trust is a framework that has evolved in the last 15 years to combat the sophisticated cyberattacks that have emerged. Zero Trust principles have been tailored for cloud environments, remote work setups, and user behaviour authentication methods to ensure adaptability and relevance. Zero Trust implementation offers multi-layered advantages. It mandates multi-factor authentication and encryption, reduces vulnerability exposure through granular authorisation, and enhances security by segmenting networks and employing dynamic access control mechanisms.
It emerged as a framework in 2010 by Forrester Research. It challenged the underlying assumption of inherent trust within networks emphasising the importance of continuous verification and cautious access. Since its emergence pioneering organisations, in the finance and government sectors, have adopted and championed Zero Trust, highlighting its practical advantages, and driving widespread recognition within the industry. Early adopters JPMorgan Chase & Co and Goldman Sachs, leading global financial institutions, leveraged the Zero Trust framework to strengthen cybersecurity by enforcing continuous verification and strict access controls.
Implementation approaches and solutions
Zero Trust offers a spectrum of implementation approaches that can be used in combination with each other or on their own.
- Identity-centric security: Focuses on verifying and allowing access for identities regardless of their location within the network.
- Network segmentation: Divides the network into isolated segments to restrict lateral movement and contain potential threats.
- Application and data-centric security: Prioritises safeguarding sensitive data through encryption and strict access controls.
- Software-defined perimeter: Establishes adaptive and secure network perimeters tailored to each user or device, granting access based on specific needs.
- Risk-based authentication: Evaluates access attempts considering associated risks, providing stronger authentication for higher-risk activities or abnormal behaviours.
The below diagram illustrates common solutions that can solve business challenges:

Figure 2: Common solutions to the business challenges
Zero Trust architecture components
Zero Trust has several key components that form the bedrock of its paradigm. The model’s key components, when woven together, create a fabric of robust defense ensuring that every facet of the network operates within a continuously verified, fortified environment.
Device trust and posture assessment: This ensures the safety and health of devices before granting access, allowing only trusted and properly secured devices into the system.
Identity and access management: They control the access to digital resources by ensuring only authorised individuals have permission, similar to giving keys to the right rooms in a house.
Data encryption: This protects sensitive data by scrambling it, allowing only authorised entities with the correct ‘key’ to access and decipher it.
Network segmentation: Creating segmented areas in a network with varying access levels, similar to different rooms in a building with different security requirements.
Secure access to applications: Setting up individual security checkpoints for applications, allowing access only to authorized users or devices.
External access points: Secure entryways for outsiders to access the network, employing strict security measures to prevent unauthorised access and potential threats.
Continuous monitoring: Constantly watching the network for unusual activities or threats, akin to having 24/7 security guards for real-time threat detection.
Policy enforcement points: Acting as security checkpoints to regulate access based on established rules, allowing, or denying access as per security policies.
Dynamic policy adaptation: Adapting security rules based on real-time network conditions, similar to adjusting traffic rules in response to immediate risks or anomalies.
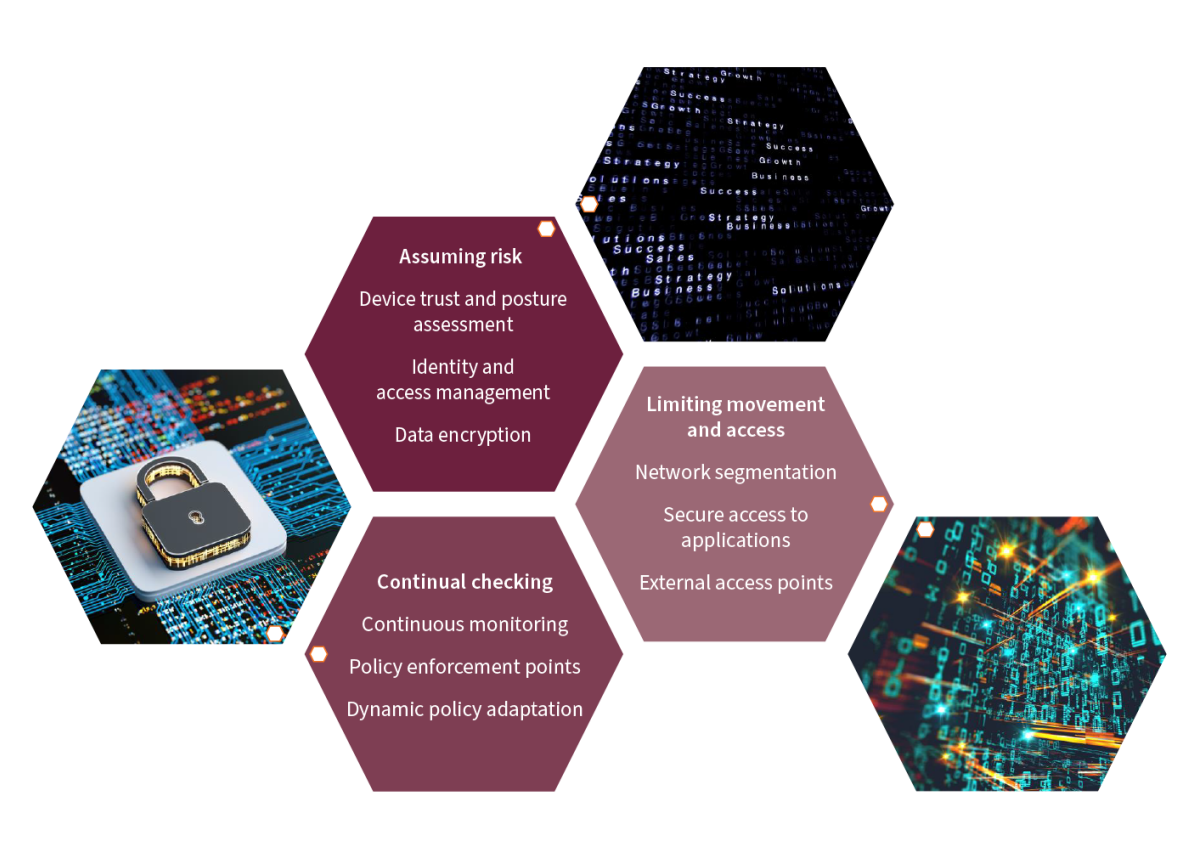
Figure 2: Zero Trust architecture and its components
The diagram above illustrates how the components of Zero Trust architecture align with the core principles of the Zero Trust framework: “Assuming Risk,” “Limiting Movement and Access,” and “Continual Checking.”
Use cases illustrating Zero Trust implementation
Use case 1: Securing high net worth individual accounts (HNWI)
Private banks manage HNWI accounts through an online platform, granting access to portfolio management, fund transfers, and investment advice from wealth managers.
Traditionally, the bank relied on perimeter-based security, but as cyberthreats advanced, including targeted phishing, sophisticated malware, and exploiting zero-day vulnerabilities, these measures became vulnerable. This leads to increased risks like unauthorised access, data breaches, and potential compromises to critical client information.
Zero trust implementation: Implementing zero-trust model, focusing on several key components, following benefits can be obtained:
- Micro-segmentation: By applying network segmentation rigorously, limiting access within the network based on the principle of least privilege. Each transaction and access request are evaluated individually.
- Continuous authentication: Enforcing multi-factor authentication (MFA) not just at login but also during transactions, ensures continuous verification of user identity.
- Behavioural analytics: Integrating advanced analytics to monitor user behaviour in real-time. Any deviation from typical usage patterns triggers immediate alerts for potential threats.
- End-to-end encryption: Encrypting all data, both at rest and in transit, safeguards it from interception or unauthorised access.
Use case 2: Account takeover
Account takeover (ATO) refers to a type of cyber-attack where a malicious actor gains unauthorised access to a user’s account, typically on an online platform or service, and takes control of it.
Account takeovers (ATO) pose a significant threat to banks, resulting in substantial financial losses. In 2021, the average ATO incident cost USD 1.3 million. ATO methods include phishing, SIM swapping, and brute force attacks, contributing to a projected ATO fraud cost exceeding USD 343 billion in the next five years. Between 2020 and 2021, ATO incidents surged by 307%, impacting both financial institutions and customer trust—seven out of ten individuals would consider leaving a brand after experiencing fraud.
Zero Trust implementation: Implementing passwordless authentication as part of Zero Trust in banks yields substantial benefits:
- Identity Theft Reduction: Up to 70% decrease in identity theft losses, particularly related to account takeovers.
- Enhanced Satisfaction: Improved customer contentment due to heightened security and smoother user experiences.
- Fraud Prevention: Preventing over USD 500,000 worth of fraud, reducing the monetary impact of fraudulent activities.
- Cost Efficiency: Approximate savings of USD 100,000 through the adoption of these secure authentication methods.
Use case 3: Account recovery
Account recovery is gaining prominence in financial institutions due to multiple factors: the proliferation of online accounts, rising cyber threat sophistication, and the heightened significance of these accounts.
Fraud affects 63% of businesses, with 25% of users experiencing account hacking. A Microsoft study found that 63% of users faced account lockouts. In banking, account recovery challenges persist, causing 20-50% of helpdesk calls to focus on password resets. Forgotten passwords frequently lead to a surge in customer support requests for resets.
Zero Trust implementation: Implementing Zero Trust’s passwordless authentication in banks offers several key advantages:
- Cost efficiency: Reducing helpdesk calls for password resets saves significant costs and curtails fraudulent transactions, potentially cutting fraud prevention expenses by 50%.
- Enhanced user experience: Simplifying account access alleviates the need for remembering passwords or frequent resets, improving customer satisfaction.
- Heightened security: Passwordless authentication challenges cybercriminals more effectively than traditional passwords, strengthening account security against unauthorised access.
Zero Trust symbolises a pivotal shift in cybersecurity ideology, promoting continual verification and adaptable security measures. Its rise signifies a proactive stance against evolving cyber threats, ushering in a transformative approach to safeguard sensitive financial data and systems. As organizations navigate these intricate challenges, it’s crucial to initiate proactive measures.
This article has navigated through the evolutionary journey of Zero Trust, delineating its milestones, adaptive frameworks, and multifaceted implementation approaches. The exploration of real-world use cases illustrates the tangible benefits of Zero Trust implementation, from securing high net worth individual accounts to mitigating threats of account takeovers and streamlining account recovery.
As the financial sector confronts a spectrum of complex challenges in safeguarding sensitive data and systems, the imperative to proactively adopt Zero Trust Strategies becomes evident. Empower your organization’s cybersecurity resilience. Schedule a consultation with our experts today to explore and address your team’s existing cybersecurity challenges effectively.


Amidst escalating cyber threats, the financial sector grapples with vulnerabilities. Dive into the transformative realm of Zero Trust, fortifying defenses and reshaping cybersecurity paradigms.
The financial industry faces a rising threat from cyberattacks, ranking high in reported data breaches. This increase is due to its speedy shift towards digital systems, inadvertently catching the attention of cybercriminals looking for weak spots in these new setups.
With heavy reliance on digital tools and more flexible work setups, there is an urgent need for better security measures. The old ways of defending these systems are not enough against the increasingly sophisticated threats targeting the various parts of the system, which include users, devices, and applications.
To tackle these challenges, a new approach called “Zero Trust” has emerged. It is a big change in how we do cybersecurity. Instead of relying on old-fashioned perimeter defences, Zero Trust acknowledges the limitations of these traditional models and focuses on finding and fixing vulnerabilities that often get overlooked.
This article will dive deeper into the overview of what Zero Trust is and how adapting a Zero Trust framework can make your organisation more secure.
Evolution and milestones of Zero Trust
Zero Trust is a framework that has evolved in the last 15 years to combat the sophisticated cyberattacks that have emerged. Zero Trust principles have been tailored for cloud environments, remote work setups, and user behaviour authentication methods to ensure adaptability and relevance. Zero Trust implementation offers multi-layered advantages. It mandates multi-factor authentication and encryption, reduces vulnerability exposure through granular authorisation, and enhances security by segmenting networks and employing dynamic access control mechanisms.
It emerged as a framework in 2010 by Forrester Research. It challenged the underlying assumption of inherent trust within networks emphasising the importance of continuous verification and cautious access. Since its emergence pioneering organisations, in the finance and government sectors, have adopted and championed Zero Trust, highlighting its practical advantages, and driving widespread recognition within the industry. Early adopters JPMorgan Chase & Co and Goldman Sachs, leading global financial institutions, leveraged the Zero Trust framework to strengthen cybersecurity by enforcing continuous verification and strict access controls.
Implementation approaches and solutions
Zero Trust offers a spectrum of implementation approaches that can be used in combination with each other or on their own.
- Identity-centric security: Focuses on verifying and allowing access for identities regardless of their location within the network.
- Network segmentation: Divides the network into isolated segments to restrict lateral movement and contain potential threats.
- Application and data-centric security: Prioritises safeguarding sensitive data through encryption and strict access controls.
- Software-defined perimeter: Establishes adaptive and secure network perimeters tailored to each user or device, granting access based on specific needs.
- Risk-based authentication: Evaluates access attempts considering associated risks, providing stronger authentication for higher-risk activities or abnormal behaviours.
The below diagram illustrates common solutions that can solve business challenges:

Figure 2: Common solutions to the business challenges
Zero Trust architecture components
Zero Trust has several key components that form the bedrock of its paradigm. The model’s key components, when woven together, create a fabric of robust defense ensuring that every facet of the network operates within a continuously verified, fortified environment.
Device trust and posture assessment: This ensures the safety and health of devices before granting access, allowing only trusted and properly secured devices into the system.
Identity and access management: They control the access to digital resources by ensuring only authorised individuals have permission, similar to giving keys to the right rooms in a house.
Data encryption: This protects sensitive data by scrambling it, allowing only authorised entities with the correct ‘key’ to access and decipher it.
Network segmentation: Creating segmented areas in a network with varying access levels, similar to different rooms in a building with different security requirements.
Secure access to applications: Setting up individual security checkpoints for applications, allowing access only to authorized users or devices.
External access points: Secure entryways for outsiders to access the network, employing strict security measures to prevent unauthorised access and potential threats.
Continuous monitoring: Constantly watching the network for unusual activities or threats, akin to having 24/7 security guards for real-time threat detection.
Policy enforcement points: Acting as security checkpoints to regulate access based on established rules, allowing, or denying access as per security policies.
Dynamic policy adaptation: Adapting security rules based on real-time network conditions, similar to adjusting traffic rules in response to immediate risks or anomalies.

Figure 2: Zero Trust architecture and its components
The diagram above illustrates how the components of Zero Trust architecture align with the core principles of the Zero Trust framework: “Assuming Risk,” “Limiting Movement and Access,” and “Continual Checking.”
Use cases illustrating Zero Trust implementation
Use case 1: Securing high net worth individual accounts (HNWI)
Private banks manage HNWI accounts through an online platform, granting access to portfolio management, fund transfers, and investment advice from wealth managers.
Traditionally, the bank relied on perimeter-based security, but as cyberthreats advanced, including targeted phishing, sophisticated malware, and exploiting zero-day vulnerabilities, these measures became vulnerable. This leads to increased risks like unauthorised access, data breaches, and potential compromises to critical client information.
Zero trust implementation: Implementing zero-trust model, focusing on several key components, following benefits can be obtained:
- Micro-segmentation: By applying network segmentation rigorously, limiting access within the network based on the principle of least privilege. Each transaction and access request are evaluated individually.
- Continuous authentication: Enforcing multi-factor authentication (MFA) not just at login but also during transactions, ensures continuous verification of user identity.
- Behavioural analytics: Integrating advanced analytics to monitor user behaviour in real-time. Any deviation from typical usage patterns triggers immediate alerts for potential threats.
- End-to-end encryption: Encrypting all data, both at rest and in transit, safeguards it from interception or unauthorised access.
Use case 2: Account takeover
Account takeover (ATO) refers to a type of cyber-attack where a malicious actor gains unauthorised access to a user’s account, typically on an online platform or service, and takes control of it.
Account takeovers (ATO) pose a significant threat to banks, resulting in substantial financial losses. In 2021, the average ATO incident cost USD 1.3 million. ATO methods include phishing, SIM swapping, and brute force attacks, contributing to a projected ATO fraud cost exceeding USD 343 billion in the next five years. Between 2020 and 2021, ATO incidents surged by 307%, impacting both financial institutions and customer trust—seven out of ten individuals would consider leaving a brand after experiencing fraud.
Zero Trust implementation: Implementing passwordless authentication as part of Zero Trust in banks yields substantial benefits:
- Identity Theft Reduction: Up to 70% decrease in identity theft losses, particularly related to account takeovers.
- Enhanced Satisfaction: Improved customer contentment due to heightened security and smoother user experiences.
- Fraud Prevention: Preventing over USD 500,000 worth of fraud, reducing the monetary impact of fraudulent activities.
- Cost Efficiency: Approximate savings of USD 100,000 through the adoption of these secure authentication methods.
Use case 3: Account recovery
Account recovery is gaining prominence in financial institutions due to multiple factors: the proliferation of online accounts, rising cyber threat sophistication, and the heightened significance of these accounts.
Fraud affects 63% of businesses, with 25% of users experiencing account hacking. A Microsoft study found that 63% of users faced account lockouts. In banking, account recovery challenges persist, causing 20-50% of helpdesk calls to focus on password resets. Forgotten passwords frequently lead to a surge in customer support requests for resets.
Zero Trust implementation: Implementing Zero Trust’s passwordless authentication in banks offers several key advantages:
- Cost efficiency: Reducing helpdesk calls for password resets saves significant costs and curtails fraudulent transactions, potentially cutting fraud prevention expenses by 50%.
- Enhanced user experience: Simplifying account access alleviates the need for remembering passwords or frequent resets, improving customer satisfaction.
- Heightened security: Passwordless authentication challenges cybercriminals more effectively than traditional passwords, strengthening account security against unauthorised access.
Zero Trust symbolises a pivotal shift in cybersecurity ideology, promoting continual verification and adaptable security measures. Its rise signifies a proactive stance against evolving cyber threats, ushering in a transformative approach to safeguard sensitive financial data and systems. As organizations navigate these intricate challenges, it’s crucial to initiate proactive measures.
This article has navigated through the evolutionary journey of Zero Trust, delineating its milestones, adaptive frameworks, and multifaceted implementation approaches. The exploration of real-world use cases illustrates the tangible benefits of Zero Trust implementation, from securing high net worth individual accounts to mitigating threats of account takeovers and streamlining account recovery.
As the financial sector confronts a spectrum of complex challenges in safeguarding sensitive data and systems, the imperative to proactively adopt Zero Trust Strategies becomes evident. Empower your organization’s cybersecurity resilience. Schedule a consultation with our experts today to explore and address your team’s existing cybersecurity challenges effectively.




